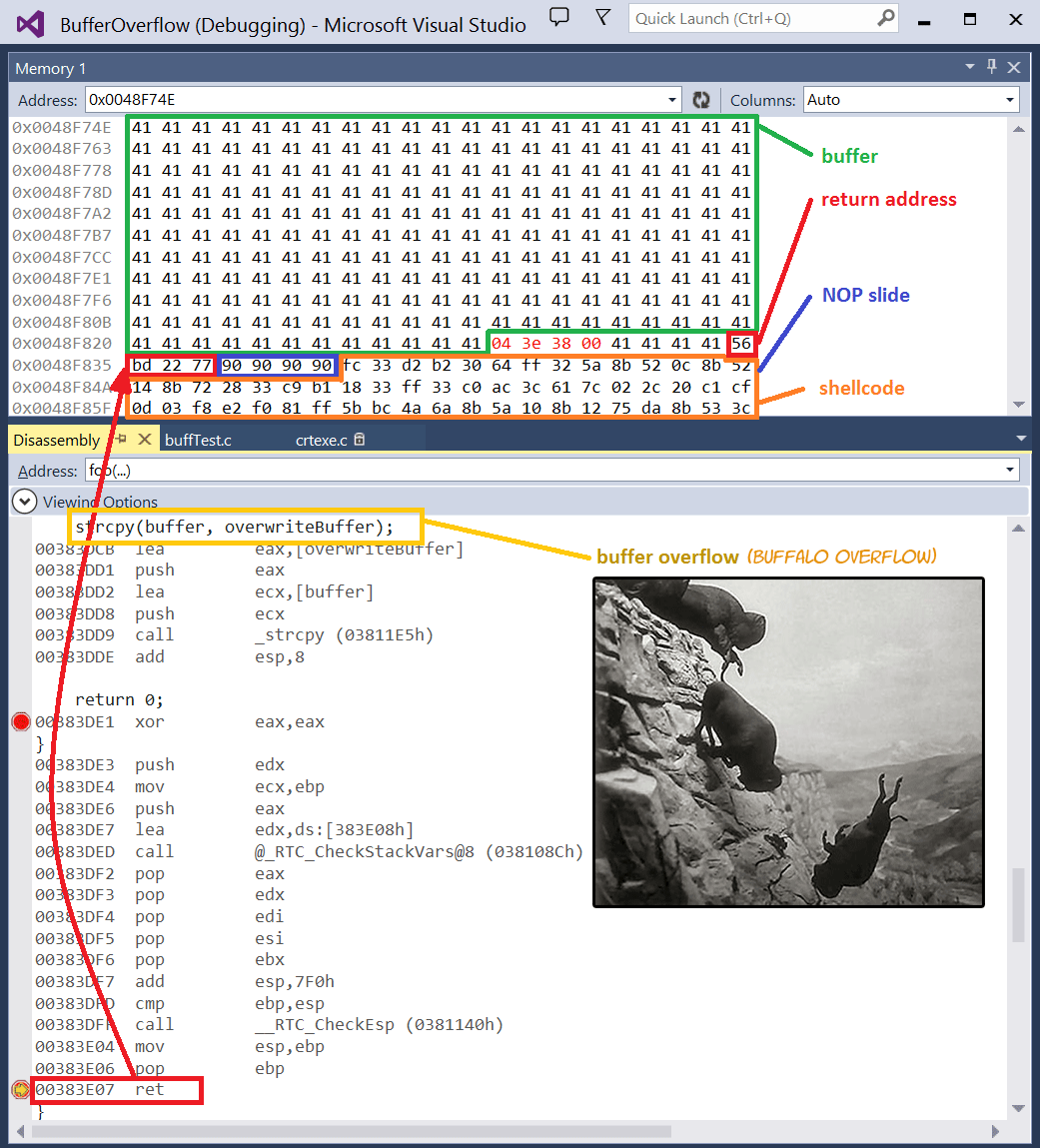
homework3 Stack-based buffer overflow-2 - CSE 610 Special Topics: System Security - Attack and Defense for Binaries Instructor: Ziming | Course Hero
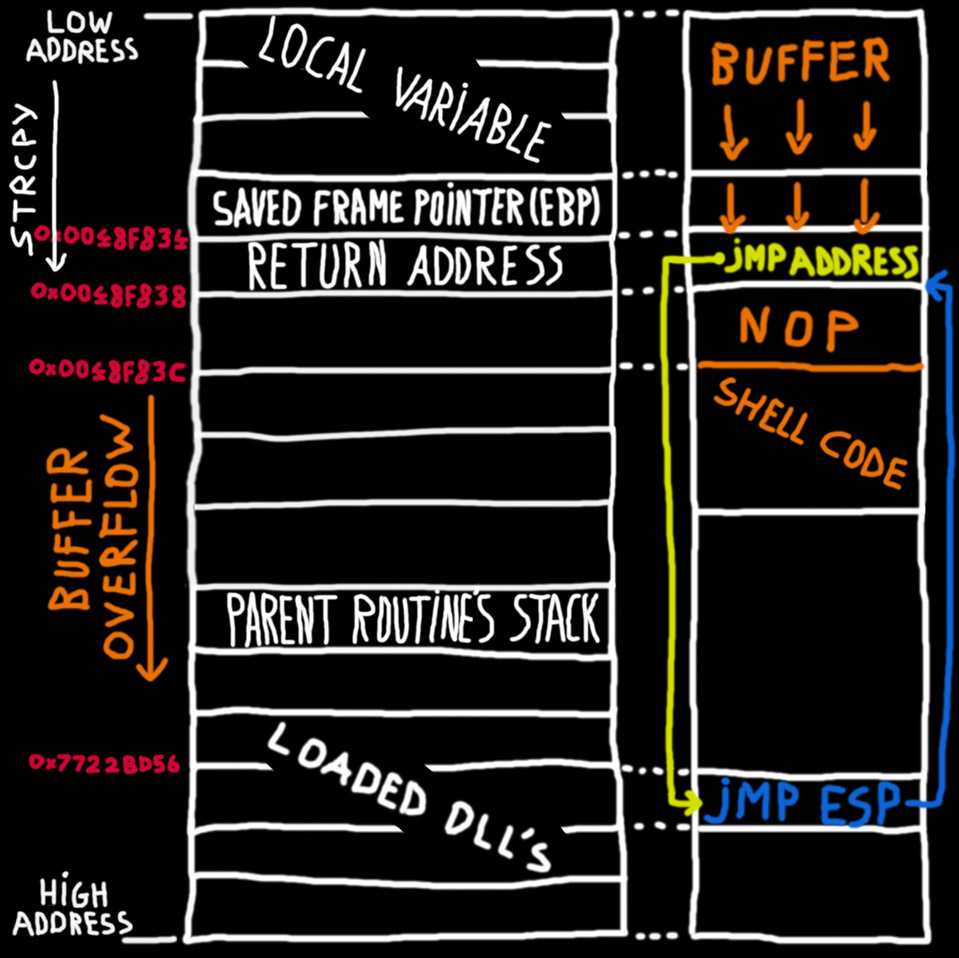
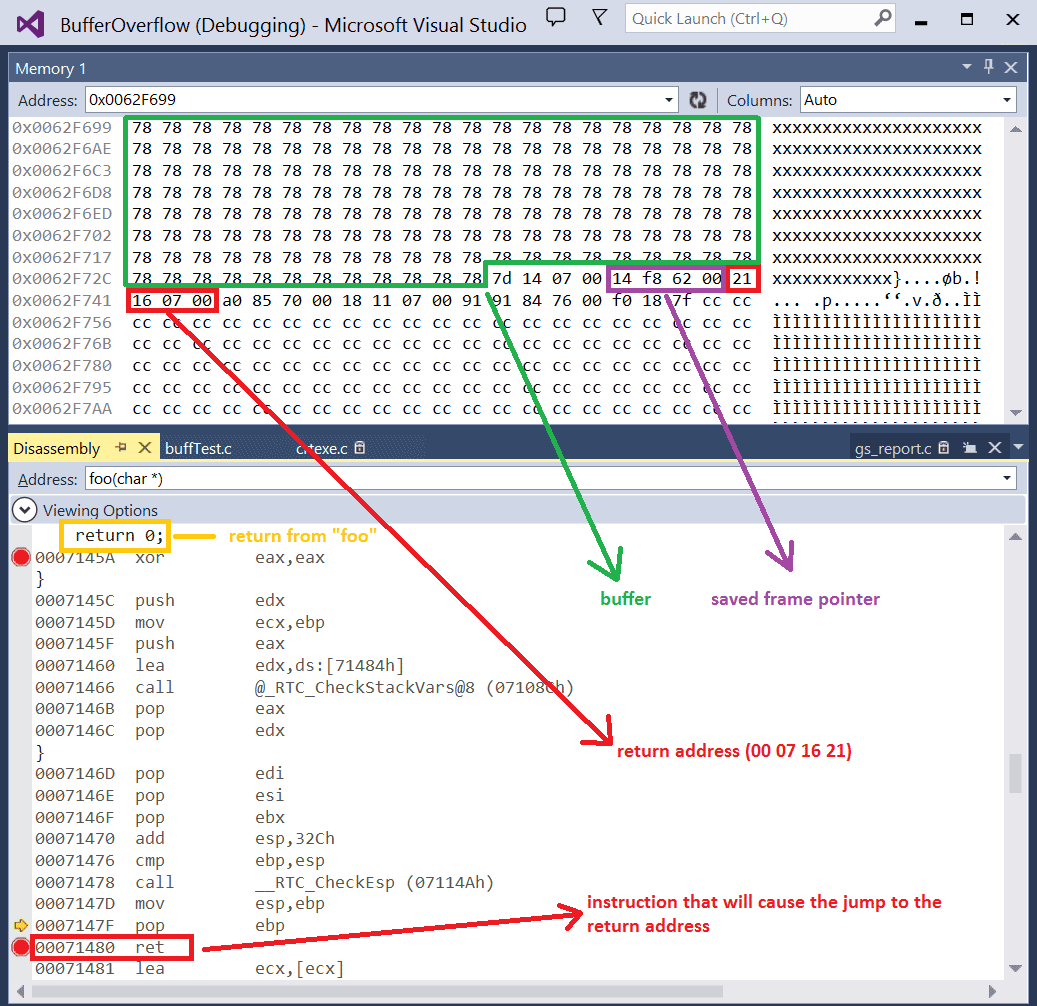
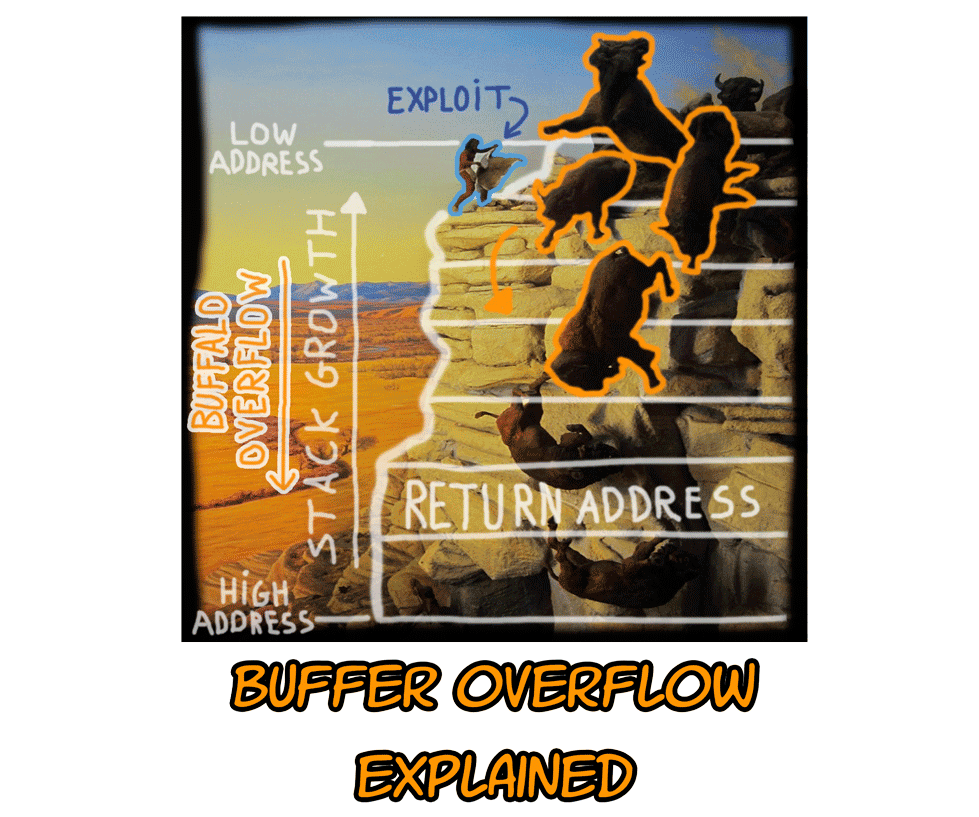
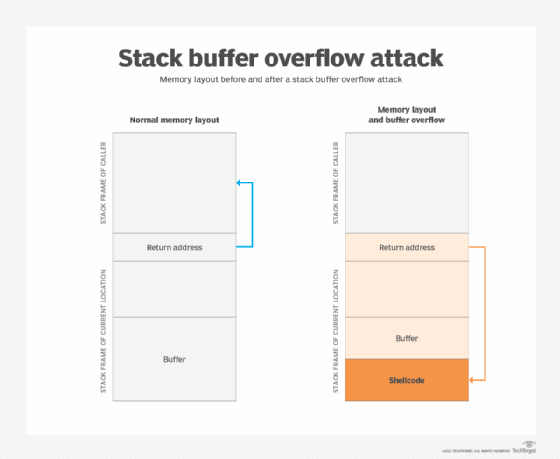
Buffer Overflow Network Security Computer Network Attack, PNG, 1240x1346px, Buffer Overflow, Area, Attack, Computer Network, Computer

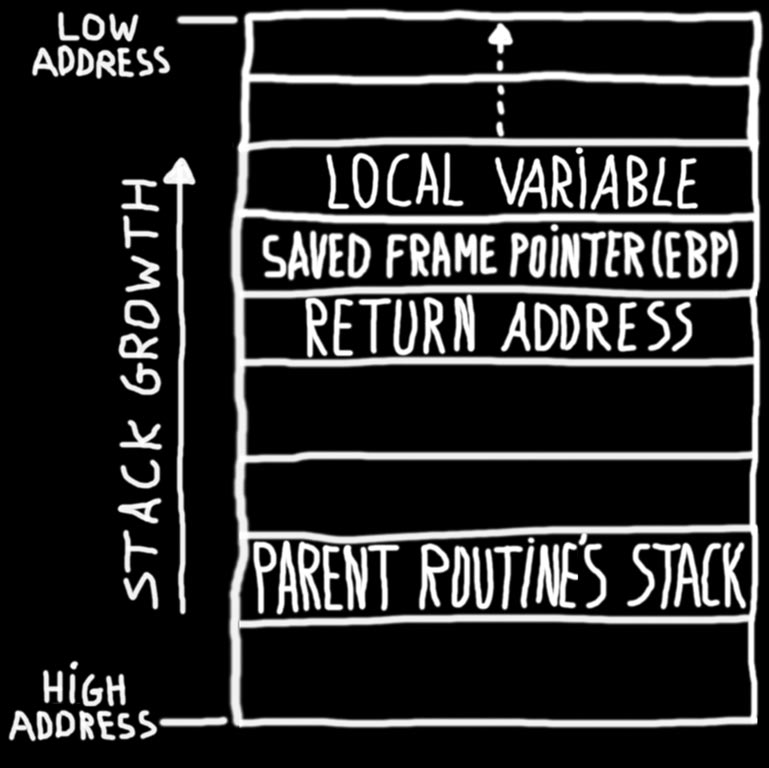
Buffer Overflow Lab.docx - Buffer Overflow Lab Based heavily on a lab developed by Wenliang Du of Syracuse University as part of the SEED labs series | Course Hero